Key Management Policy Template - This policy and standard apply to. Ensure that reveal consistently follows industry standards for encryption and key management. General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption.
This policy and standard apply to. Ensure that reveal consistently follows industry standards for encryption and key management. General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption.
General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption. Ensure that reveal consistently follows industry standards for encryption and key management. This policy and standard apply to.
Key Management Policy Template
This policy and standard apply to. Ensure that reveal consistently follows industry standards for encryption and key management. General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption.
Encryption Key Management Policy Template
Ensure that reveal consistently follows industry standards for encryption and key management. This policy and standard apply to. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption. General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used.
ISO 27001 Cryptographic Key Management Policy Template
General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption. Ensure that reveal consistently follows industry standards for encryption and key management. This policy and standard apply to.
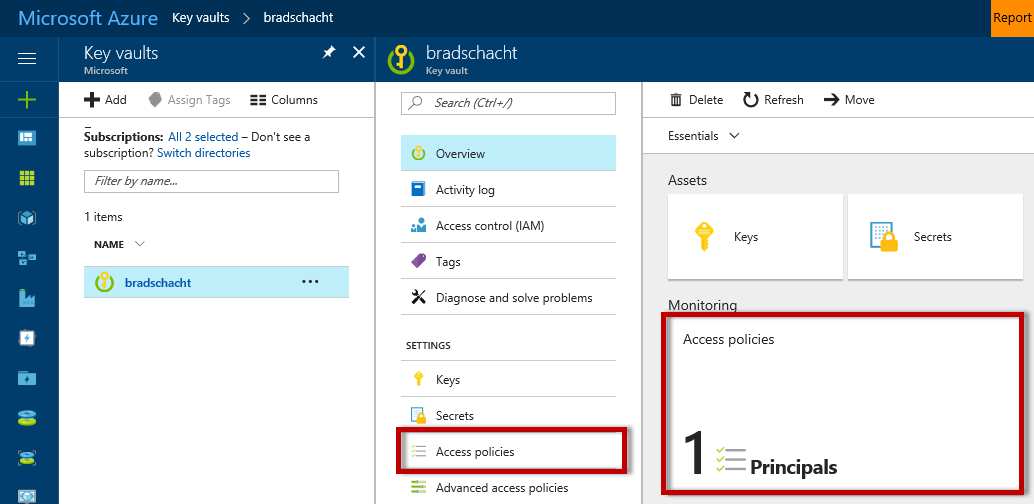
Amazing Encryption Key Management Policy Template Sparklingstemware
General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used. Ensure that reveal consistently follows industry standards for encryption and key management. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption. This policy and standard apply to.
ISO 27001 Cryptographic Key Management Policy Template
This policy and standard apply to. General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used. Ensure that reveal consistently follows industry standards for encryption and key management. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption.
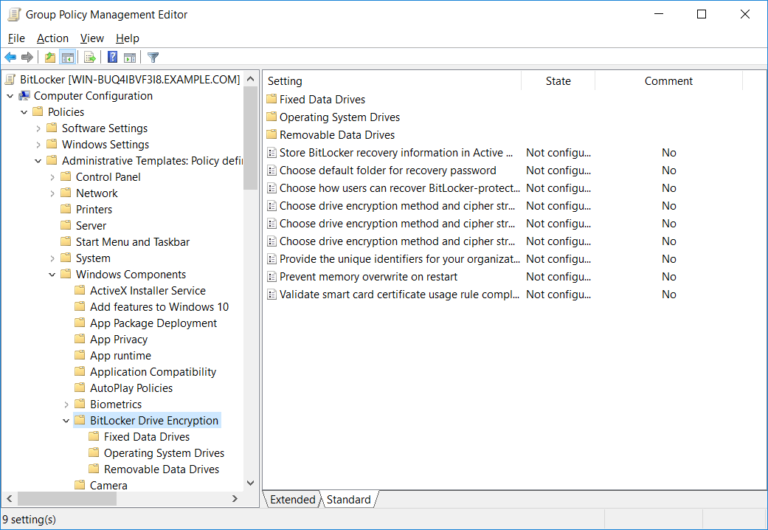
Fascinating Encryption Key Management Policy Template Sparklingstemware
Ensure that reveal consistently follows industry standards for encryption and key management. This policy and standard apply to. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption. General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used.
ISO 27001 Cryptographic Key Management Policy Template
General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used. Ensure that reveal consistently follows industry standards for encryption and key management. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption. This policy and standard apply to.
ISO 27001 Cryptographic Key Management Policy Template
This policy and standard apply to. General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption. Ensure that reveal consistently follows industry standards for encryption and key management.
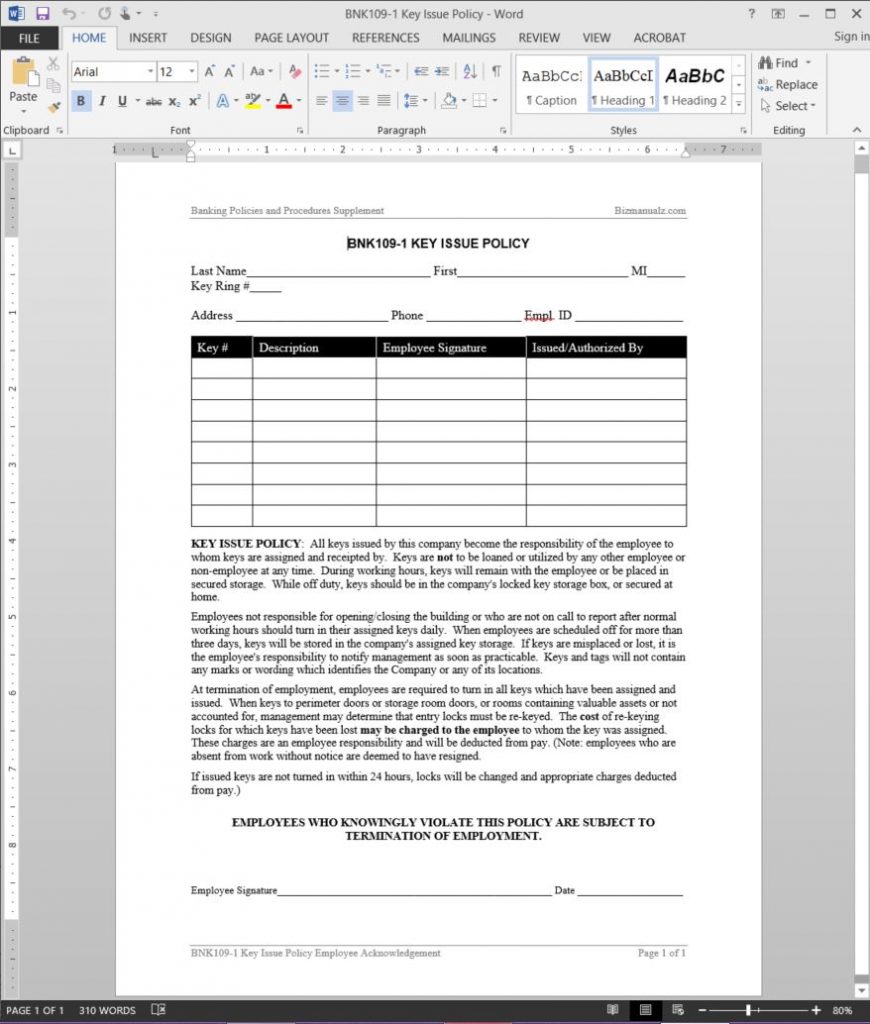
Amazing Key Control Policy Template Policy template, Functional group
Ensure that reveal consistently follows industry standards for encryption and key management. This policy and standard apply to. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption. General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used.
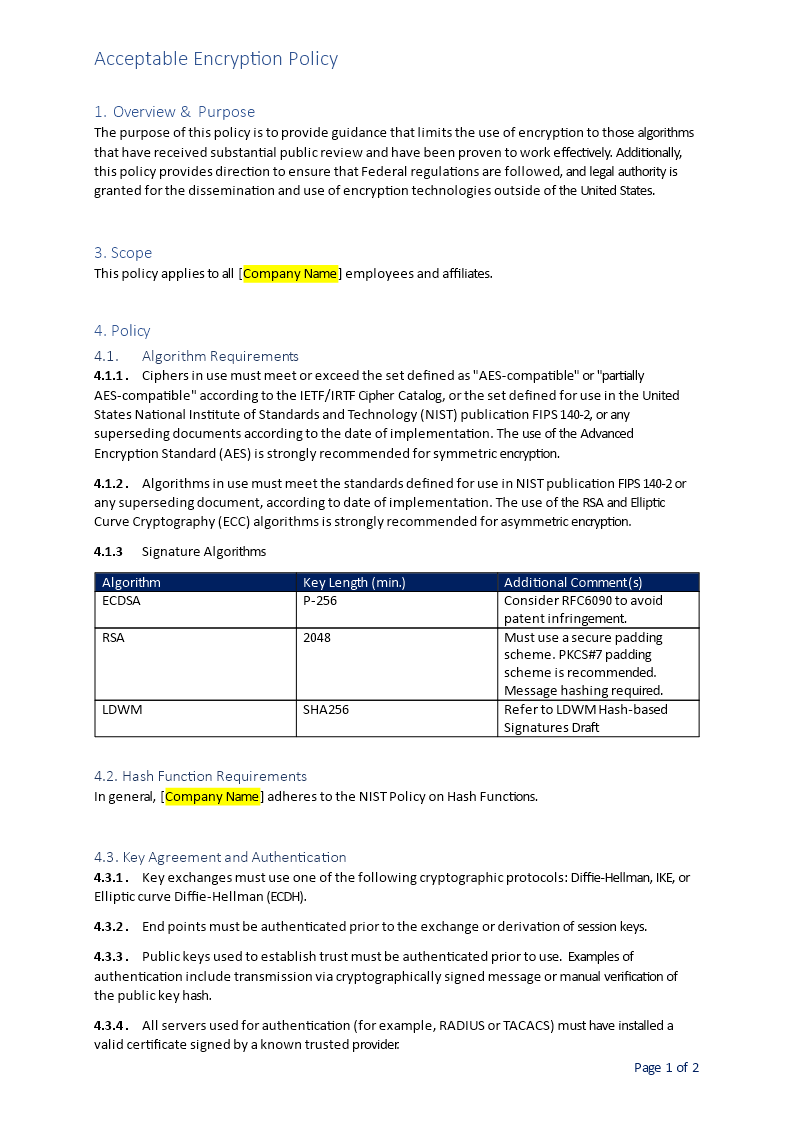
Encryption Key Management Policy Template Policy template, Management
Ensure that reveal consistently follows industry standards for encryption and key management. General requirements for the key management process must be defined to ensure appropriate secure management of cryptographic keys used. This policy and standard apply to. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption.
General Requirements For The Key Management Process Must Be Defined To Ensure Appropriate Secure Management Of Cryptographic Keys Used.
Ensure that reveal consistently follows industry standards for encryption and key management. Cio 2100.1, “gsa information technology (it) security policy.” when used to protect sensitive information, federal systems must use encryption. This policy and standard apply to.